Introduction To Software Exploits
Creator: Corey Kallenberg @CoreyKal
License: Creative Commons: Attribution, Share-Alike
(http://creativecommons.org/licenses/by-sa/3.0/)
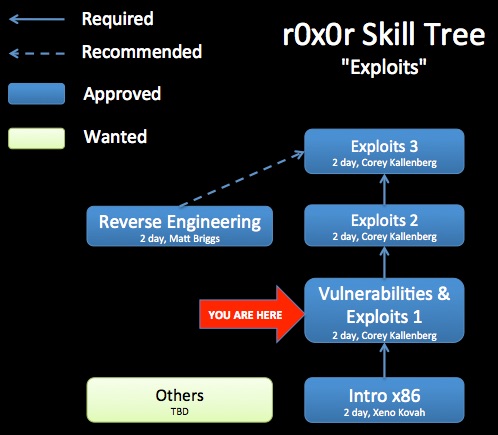
Class Prerequisites: Introduction to x86
Lab Requirements: The Linux VM provided below. Or any Linux VM with the provided vulnerable software examples installed.
Class Textbook: "The Shellcoder's Handbook: Discovering and Exploiting Security Holes" (2nd edition) by Chris Anley, John Heasman, Felix Lindner, Gerardo Richarte
Recommended Class Duration: 2 days
Creator Available to Teach In-Person Classes: Yes
Author Comments:
Software vulnerabilities are flaws in program logic that can be leveraged by an attacker to execute arbitrary code on a target system. This class will cover both the identification of software vulnerabilities and the techniques attackers use to exploit them. In addition, current techniques that attempt to remediate the threat of software vulnerability exploitation will be discussed.
This will be a lab driven class where specific software vulnerability types in particular environments are discussed and then exploited in a lab setting. Examples of lab components of the class as well as specific topics covered include:
•Shellcode development
•Stack overflow exploitation
•Heap overflow exploitation
•Static source code analysis
•Defeating non-executable stack protection
The class will help students be more aware of the specific details and mechanisms of software exploits we see in the wild. This knowledge will enable the students to better analyze their own software for vulnerabilities in an effort to produce more secure code.
Author Biography:
Corey Kallenberg co-founded LegbaCore in January 2015 to focus on improving firmware security. He has a Bachelors of Science in Computer Science from the University of Waterloo. His specialty areas are trusted computing, vulnerability research and low level development. In particular, Corey has spent several years using his vulnerability research expertise to evaluate limitations in current trusted computing implementations. In addition, he has used his development experience to create and improve upon trusted computing applications. Among these are a timing based attestation agent designed to improve firmware integrity reporting, and an open source Trusted Platform Module driver for Windows. Corey is also an experienced trainer, having created and delivered technical courses for the MITRE Institute, OpenSecurityTraining.info, CanSecWest, as well as numerous private customers. He is an internationally recognized speaker who has presented at BlackHat USA, DEF CON, CanSecWest, Hack in the Box KUL/AMS/GSEC, SummerCon, NoSuchCon, SyScan, EkoParty and Ruxcon. In 2015, Corey won the Pwnie award for best privilege escalation bug, for CERT VU# 552286, which exploits from userspace (ring 3) to SMM (ring “-2”), and which was found on hundreds of models of computers.

Class Materials
-
-zip password = “Exploits1”, accounts are student/student and root/root
-
-md5 = c7e628f55b3416c280b949e2292ba98e
-
-about 1.4GB compressed, about 5GB uncompressed

Day 1 Part 1 (58:59, 687 MB)
Day 1 Part 2 (39:51, 494 MB)
Day 1 Part 3 (59:07, 704 MB)
Day 1 Part 4 (34:36, 340 MB)
Day 1 Part 5 (36:19, 381 MB)
Day 1 Part 6 (56:25, 636 MB)
Day 2 Part 1 (44:21, 465 MB)
Day 2 Part 2 (51:41, 586 MB)
Day 2 Part 3 (1:02:23, 679 MB)
Day 2 Part 4 (1:05:22, 657 MB)
Day 2 Part 5 (1:09:50, 791 MB)
(9:38:54 total, sans lab time)
The videos are useful for students, but also more useful for potential instructors who would like to teach this material. By watching the video, you will better understand the intent of some slides which do not stand on their own. You are recommended to watch the largest size video so that the most possible text is visible without having to follow along in the slides.

Revision History:
07-07-2012 - Uploaded full quality downloadable videos to Archive.org
06-20-2012 - Day 2 videos uploaded to Youtube
05-16-2012 - Day 1 videos uploaded to Youtube
06-07-2011 - Initial class content upload
If you have used and modified this material, we would appreciate it if you submit your modified version for publishing here, so that all versions can benefit from your changes.